Hey,
If you are using paid email services, you may ask your service provider to block similar sources or else only way to do so is manual filtering as described below-
There are many reasons in today’s environment to be wary of email that seems in any way suspicious. Some email messages might be phishing scams; some might contain viruses and other malicious software. Files within the messages can contain inappropriate images and include web beacons, which can be used to secretly send a message back to the sender.
If an email looks suspicious, don’t risk your personal information by opening or responding to the message. Below are some suggested guidelines to help protect yourself against these threats when suspicious mail arrives within your mailbox:
- If you receive a phishing e-mail message, do not respond to it. Don’t open junk mail at all
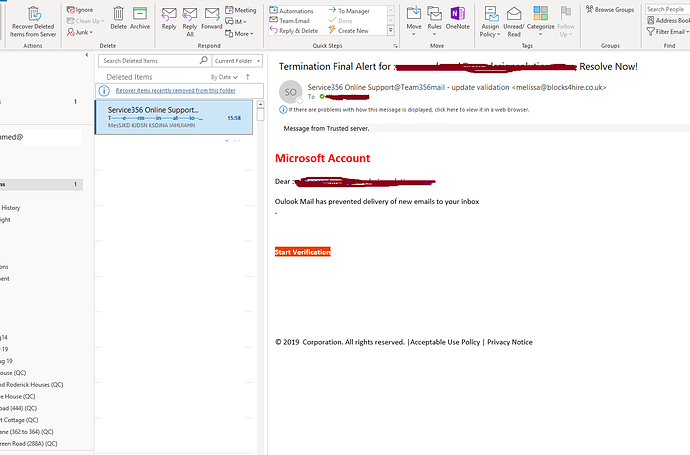
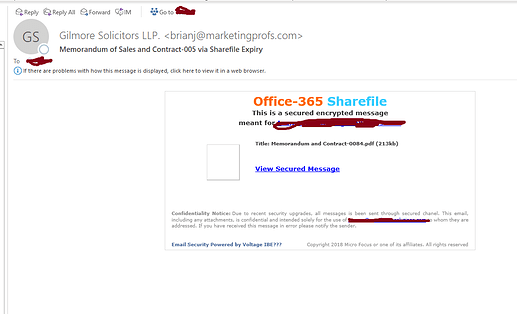
First off, what is Phishing (pronounced “fishing”)? It is a type of online identity theft that uses e-mail and fraudulent websites that are designed to steal your personal data or information such as credit card numbers, passwords, account data or other information. To protect yourself from phishing scams sent through e-mail, if an email looks suspicious, don’t risk your personal information by responding to it. Delete junk email messages without opening them. Sometimes even opening spam can alert spammers or put an unprotected computer at risk. Don’t reply to email unless you’re certain that the message comes from a legitimate source. This includes not responding to messages that offer an option to “Remove me from your list.” Do not “unsubscribe” unless the mail is from a known or trusted sender. Use the junk mail tools in your e-mail program.
- Approach links in email messages with caution
Links in phishing email messages often take you to phony sites that encourage you to transmit personal or financial information to con artists. Avoid clicking a link in an email message unless you are sure of the real target address, URL, or a valid sender.
Most e-mail programs show you the real target address of a link when you hover the mouse over the link within the message.
Before you click a link, make sure to read the target address. If the email message appears to come from your bank, but the target address is just a meaningless series of numbers, do not click the link.
Make sure that the spelling of words in the link matches what you expect. Spammers and scammers often use URLs with typos and transposed letters in them that are easy to overlook, such as “Retdail.”
- Approach images in e-mail with caution
Just as a beacon within the oceans transmits a message or data back to a source, images within email messages —also known as “web beacons” — can be used to secretly send a message back to the sender.
Spammers rely on information returned by these images to locate active e-mail addresses. Images can also contain harmful codes and can be used to deliver a spammer’s message in spite of filters.
The best defense against web beacons is to prevent pictures from downloading until you’ve had a chance to review the message. Most offline mail clients include these settings.
- Approach attachments in email messages with caution
Attachments might be viruses or spyware that download to your machine when you open the attachment file. If you don’t know whom the attachment is from or if you weren’t expecting it, DO NOT open the attachment.
- Don’t trust the sender information in an e-mail message
Even if the email message appears to come from a particular sender that you know and trust, use the same precautions that you would use with any other email message. Spoofing is email activity in which the sender address and other parts of the email header are altered to appear as though the email originated or was sent from a different source. This is a common practice of spammers and is one of the hardest to combat as there may be legitimate reasons to spoof an address.
- Don’t trust offers that seem too good to be true
If a deal or offer in an email message looks too good to be true, it probably is. The best defense is to exercise your common sense when you read and respond to email messages.
- Report suspicious email
If you receive a suspicious email that looks like it came from a company that you know and trust, report the email to the faked or “spoofed” organization.
Contact the organization directly (not through the email you received) and ask for confirmation on the validity of the message. Or call the organization’s toll-free number and speak to a customer service representative.
- Don’t enter personal or financial information into pop-up windows
One common phishing technique is to launch a fake pop-up window when someone clicks a link in a phishing e-mail message. To make the pop-up window look more convincing, it might be displayed over a window you trust. Even if the pop-up window looks official or claims to be secure, avoid entering sensitive information, because there is no way to check the security certificate. Close pop-up windows by clicking the red X in the top right corner as the “Cancel” button may not work as you’d expect it would.
- Don’t forward chain email messages
Not only do you lose control over who sees your email address making your address susceptible to attacks, but you also may be furthering a hoax or aiding in the delivery of a virus.
Additionally, there are reports that spammers start chain letters expressly to gather email addresses to spam. If you don’t know whether a message is a hoax or not, a site like Snopes.com can help you separate fact from fiction or a Google search of the message can help you determine the validity.
- Update your computer software including OS upgrades, patches, Anti-virus, etc.